
How to deploy weaviate to google cloud using Kubernetes
Weaviate is a powerful vector database designed for AI applications. When deploying it in production, security is paramount. This guide covers:
Initial deployment of Weaviate on Kubernetes
Setting up API key authentication
Implementing HTTPS/TLS encryption with Let's Encrypt
Configuring Ingress for proper routing
Prerequisites
- A running Kubernetes cluster (GKE in this example)
- google cloud account with credits
- kubectl command-line tool configured
- A domain name with DNS access (we used sehajbindra.info)
Step : 1 Setup
Go to the google cloud marketplace and search for weaviate.
- After purchasing we need to configure the Installation Instructions
- To deploy Weaviate, follow these steps:
- Navigate to Weaviate's Google Cloud Marketplace listing page and click Configure.
- Follow the on-screen instructions to configure and deploy Weaviate.
Configuration Options
Before starting the deployment, consider the following configuration options:
Suggested Configurations
- Default values for settings like Global Query Limit, Modules, and Storage Size are generally suitable for most use cases.
- For production environments, a minimum of 500GB storage per pod is recommended, while smaller disks may suffice for development environments.
- Once on the deployment page, you will encounter several options:
- Select a GKE cluster for Weaviate deployment. You can create a new cluster if needed.
- Specify the namespace for resource division and a unique app instance name for identification.
- Set the service account for billing purposes.
- Configure Weaviate parameters, including Replicas of Weaviate Instances, Global Query Limit, Enable Modules, and Storage Size.
- Accept the terms of service and click Deploy.
- After completing these steps, Weaviate will be deployed to your selected cluster, which may take a few minutes.Verifying the Initial Weaviate Deployment.
Verifying the Initial Weaviate Deployment
First, let's check if Weaviate is properly deployed:
1kubectl get svc --all-namespacesYou should see Weaviate services running with external IPs:
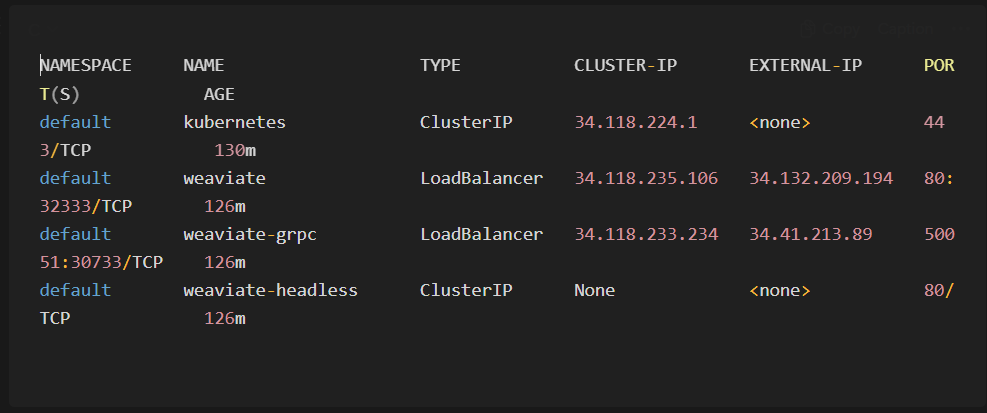
Note: if you are not getting the weaviate services here it means weaviate is not deployed at first place. For more info read this.
Step: 2 Setting Up Authentication for Weaviate on Kubernetes
Weaviate supports several authentication methods, but API key authentication is one of the simplest to implement. It allows you to secure your Weaviate instance with minimal configuration while providing a straightforward way for applications to authenticate.
Prerequisites
Before starting, ensure you have:
- A running Kubernetes cluster
- Weaviate installed on the cluster
- kubectl configured to access your cluster
- Admin access to modify Kubernetes resources
(A) Generate a Secure API Key
First, generate a secure random API key. You can use OpenSSL for this:
1API_KEY=$(openssl rand -base64 32)
2echo $API_KEYThis will output a secure random string like:
18sxbmxxxxxxxxxxxxxxSave this key securely as you'll need it for authentication.
(B) Configure Authentication in Weaviate
To enable API key authentication in Weaviate, we need to add environment variables to the Weaviate StatefulSet.
Create a Kubernetes Secret for the API key
1kubectl create secret generic weaviate-auth-secret --from-literal=api-key="admin=YOUR_API_KEY"
2# replace with the api key you created using open ssl.(C) Update your Weaviate configuration
1kubectl get statefulsetGood to know: A StatefulSet is a Kubernetes workload API object used to manage stateful applications that require stable network identities, persistent storage, and ordered deployment.
1️⃣ Stable Network Identity: Each pod gets a unique, predictable name (pod-0, pod-1, pod-2).
2️⃣ Persistent Storage: Each pod gets its own Persistent Volume (PV), which is not shared with other pods.
You will get output of the pods:
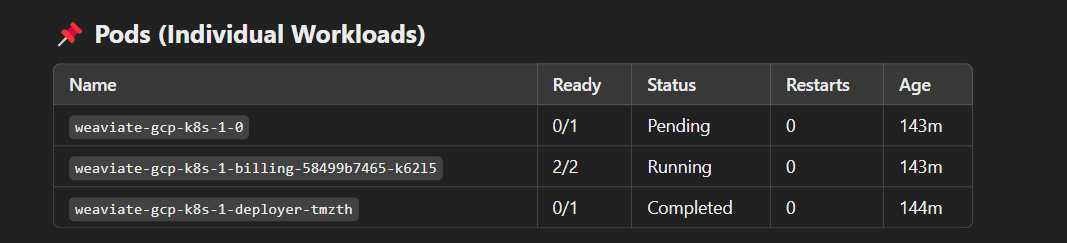
Then update the StatefulSet with your configuration:
1kubectl edit statefulset weaviate-gcp-k8s-1Replace the authentication environment variables with:
Then, in the editor, add these environment variables in the env: section under the container definition (place them with the other env vars):
When editing a Kubernetes resource with the kubectl edit command, you'll be placed in a text editor (usually Vim or Nano, depending on your system's default editor). Here's how to edit the file in the editor:
When editing a Kubernetes resource with the kubectl edit command, you'll be placed in a text editor (usually Vim or Nano, depending on your system's default editor). Here's how to edit the file in the editor:
If you're using Vim (most common default)
- When the file opens, you'll be in "command mode"
- Press i to enter "insert mode" where you can make changes
- Use arrow keys to navigate to the right position (where the other env variables end)
- Add your new environment variables with proper indentation
- When finished, press Esc to exit insert mode
- Type :wq and press Enter to save and quit
If you're using Nano
- Use arrow keys to navigate to where you want to add the environment variables
- Type or paste the new environment variables
- Press Ctrl+O then Enter to save
- Press Ctrl+X to exit
1- name: AUTHENTICATION_APIKEY_ENABLED
2 value: "true"
3- name: AUTHENTICATION_APIKEY_USERS
4 value: "admin"
5- name: AUTHENTICATION_APIKEY_ALLOWED_KEYS
6 valueFrom:
7 secretKeyRef:
8 name: weaviate-auth-secret
9 key: api-key
10- name: AUTHENTICATION_ANONYMOUS_ACCESS_ENABLED
11 value: "false"(D) Apply the Changes
After editing the StatefulSet, Kubernetes will automatically update the pods with the new configuration. You can get the pods:
1kubectl get podsIf you see pods in an error state, check the logs
1kubectl logs <pod-name>(E) Verify Authentication is Working
Once your Weaviate pods are running, test the authentication:
Try accessing Weaviate without authentication (should fail)
1curl -X GET "http://<weaviate-external-ip>/v1/meta" \
2 -H "Content-Type: application/json"Try accessing Weaviate with authentication (should succeed)
1curl -X GET "http://<weaviate-external-ip>/v1/meta" \
2 -H "Authorization: Bearer YOUR_API_KEY \
3 -H "Content-Type: application/json"Authorization Fails Despite Correct Configuration
If authentication is configured but API requests still fail:
- Double-check the API key for typos or whitespace
- Ensure the Authorization header is formatted correctly: Bearer <api-key>
- Check if the Weaviate service is properly exposing port 80
Step 3: Implementing HTTPS/TLS with Let's Encrypt
(A) Install NGINX Ingress Controller
TLS Architecture Overview
For production deployments, a proper TLS setup includes:
- Ingress Controller: Handles traffic routing and TLS termination
- Certificate Manager: Automates certificate provisioning and renewal
- TLS Certificates: Secures all communications
1kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/controller-v1.8.2/deploy/static/provider/cloud/deploy.yamlVerify deployment:
1kubectl get pods -n ingress-nginx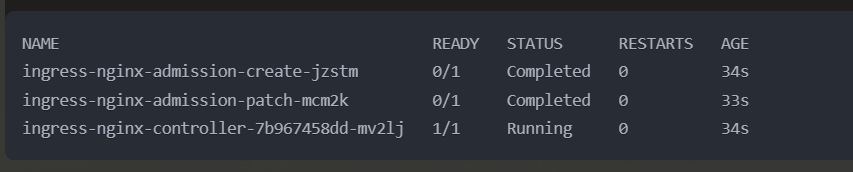
Check the service to get the external IP:
1kubectl get svc -n ingress-nginx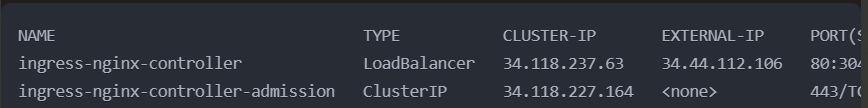
(B) Install cert-manager
cert-manager handles certificate issuance and renewal automatically:
1kubectl apply -f https://github.com/cert-manager/cert-manager/releases/download/v1.13.2/cert-manager.yamlVerify installation:
1kubectl get pods -n cert-manager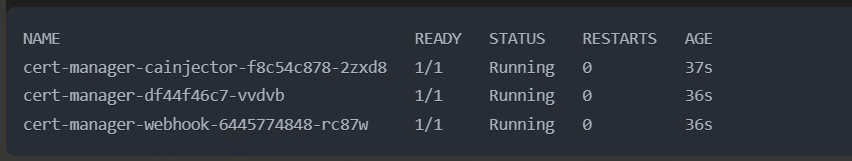
(C) Domain Configuration
- For production environments, proper DNS configuration is critical:
- Register a domain name (e.g., sehajbindra.info)
- Configure an A record pointing to your Ingress Controller's IP:
1Type: A
2Host: @ (for root domain)
3Value: 34.44.112.106 # replace with your Ip
4TTL: 3600(D) Create a Let's Encrypt ClusterIssuer
1cat <<EOF | kubectl apply -f -
2apiVersion: cert-manager.io/v1
3kind: ClusterIssuer
4metadata:
5 name: letsencrypt-prod
6spec:
7 acme:
8 server: https://acme-v02.api.letsencrypt.org/directory
9 email: your-email@example.com
10 privateKeySecretRef:
11 name: letsencrypt-prod
12 solvers:
13 - http01:
14 ingress:
15 class: nginx
16EOFMake sure to replace your-email@example.com with your actual email address before running the command.
(E) Create an Ingress Resource
1cat <<EOF | kubectl apply -f -
2apiVersion: networking.k8s.io/v1
3kind: Ingress
4metadata:
5 name: weaviate-ingress
6 namespace: default
7 annotations:
8 kubernetes.io/ingress.class: "nginx"
9 cert-manager.io/cluster-issuer: "letsencrypt-prod"
10 nginx.ingress.kubernetes.io/ssl-redirect: "true"
11 nginx.ingress.kubernetes.io/proxy-body-size: "0"
12spec:
13 tls:
14 - hosts:
15 - sehajbindra.info
16 secretName: weaviate-tls
17 rules:
18 - host: sehajbindra.info
19 http:
20 paths:
21 - path: /
22 pathType: Prefix
23 backend:
24 service:
25 name: weaviate
26 port:
27 number: 80
28EOFNow, let's check the status of the Ingress resource and the certificate:
1kubectl get ingress weaviate-ingresskubectl get ingress weaviate-ingress:
1kubectl get certificateIf the certificate shows as ready:
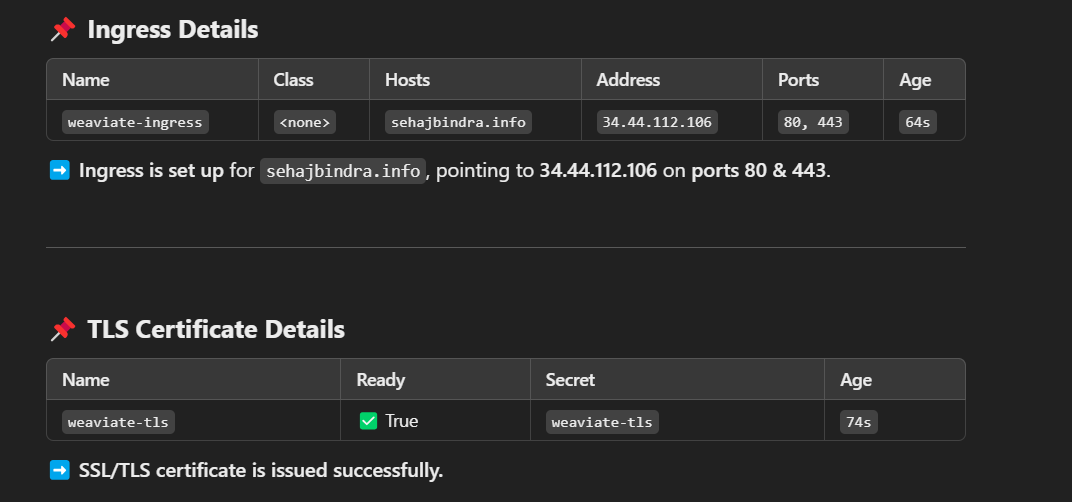
Congratulations! Your Weaviate instance is now accessible securely:
1https://sehajbindra.infoConclusion
- You now have a production-ready Weaviate installation with:
- API key authentication for secure access control
- HTTPS/TLS encryption with valid certificates from Let's Encrypt
- Proper Kubernetes resource configuration
- This setup provides a secure foundation for using Weaviate as a vector database in AI applications, ensuring that both your data and communications are protected.